DNS feels boring until it betrays you. Even with HTTPS everywhere, your resolver still sees the domains you ask for, when you ask, and how often. That trail can reveal more than the page content itself. Consequently, modern DNS hardening needs two different things at once: privacy on the wire and integrity of the answers.
This guide breaks down DoH vs DoT vs DNSSEC with an intermediate-to-advanced lens, then it recommends a “best setup” that holds up in real networks.
Why DNS privacy is still a problem
Classic DNS runs in plaintext over UDP or TCP. Anyone on-path can observe your queries. In many networks, they can also rewrite the answers. That creates three common risks:
- Passive surveillance: Wi‑Fi operators and ISPs can log queried domains and build behavioral profiles.
- Active manipulation: on‑path actors can inject responses and redirect traffic to malicious infrastructure.
- Policy entanglement: enterprises often intercept DNS for filtering which collides with privacy goals.
The IETF captured these risks years ago and the analysis still holds because DNS remains metadata-rich and frequent. See RFC 7626 for the canonical framing of DNS privacy threats: https://www.rfc-editor.org/rfc/rfc7626.html
Stop conflating them: confidentiality vs integrity vs governance
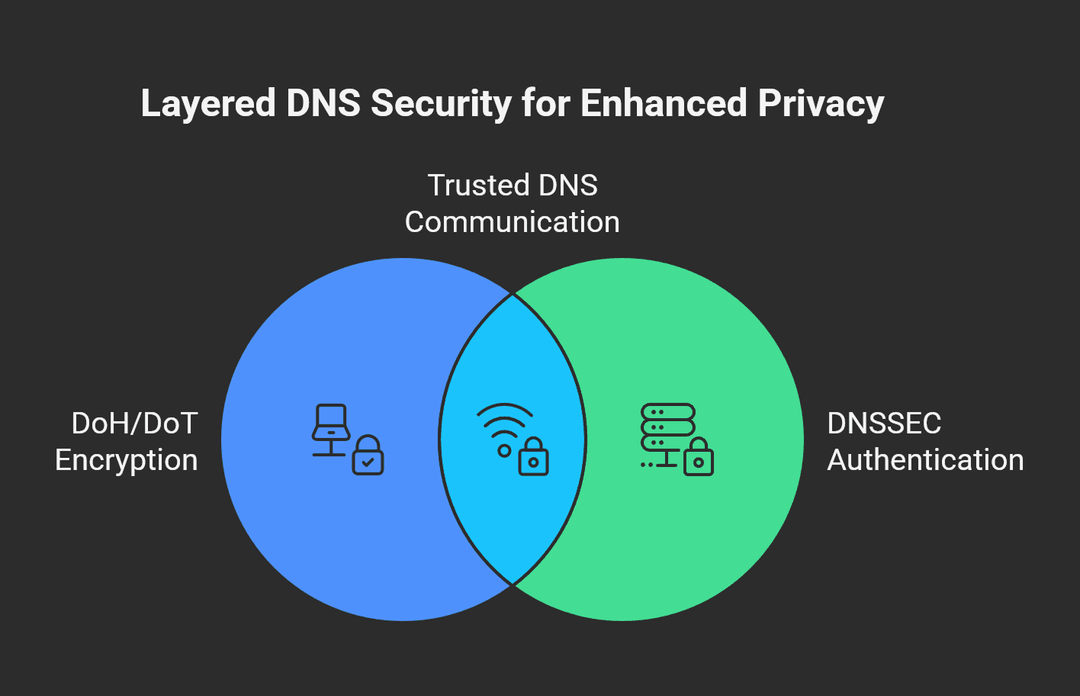
Experts get tripped up when they treat “encrypted DNS” as a single knob. It isn’t.
- DoT and DoH primarily provide transport confidentiality. They hide queries from local observers between a client and a resolver. They do not inherently prove the data came from the authoritative zone.
- DNSSEC provides data integrity and origin authentication. It prevents tampering and spoofing when validators check signatures. It does not hide what you ask for.
Governance sits above both. Somebody still operates the resolver. That operator can log queries and correlate identifiers. Encryption moves visibility from your local network to your chosen resolver. You improve privacy against on‑path observers while you concentrate trust elsewhere.
DoT explained: encrypted DNS with a dedicated channel
What DoT is
DNS over TLS (DoT) encrypts DNS traffic inside a TLS tunnel, typically on port 853. The core spec lives in RFC 7858: https://datatracker.ietf.org/doc/html/rfc7858
In practice, you run one of these patterns:
- Stub → recursive over TLS: your device sends encrypted queries to a resolver.
- Local resolver → upstream over TLS: your LAN resolver handles clients locally, then forwards upstream over TLS.
Authentication and usage profiles matter
TLS encryption without strong authentication still leaves gaps. You need to know you connected to the resolver you intended. RFC 8310 defines operational profiles and guidance for authentication: https://www.rfc-editor.org/rfc/rfc8310.html
That profile thinking becomes crucial in enterprise deployments where “some TLS” can degrade into “TLS to whoever answers first.”
DoT strengths and tradeoffs
DoT’s clean separation from web traffic makes it easier to reason about and easier to monitor responsibly. Conversely, the dedicated port also makes it easier to block. Some networks block 853 by policy or by accident.
DoH explained: DNS inside HTTPS and why it changes everything
What DoH is
DNS over HTTPS (DoH) sends DNS queries inside HTTPS requests, usually over port 443. The defining standard is RFC 8484: https://www.rfc-editor.org/rfc/rfc8484.html
DoH inherits properties from the HTTP ecosystem. That sounds convenient and it is, but it also shifts who controls DNS decisions.
DoH strengths and tradeoffs
DoH blends into normal HTTPS traffic. That makes it resilient in hostile networks where on‑path actors interfere with DNS. It also means defenders lose some network-level visibility unless endpoints cooperate.
Operationally, DoH often lives in browsers first. That can create “split DNS” where the browser uses one resolver and the OS uses another. That split undermines troubleshooting and it can leak queries through fallback paths.
DNSSEC explained: integrity that encrypted transports do not provide
What DNSSEC guarantees
DNSSEC signs DNS data so a validator can verify it came from the zone owner and it was not modified. It protects users against forged records and cache poisoning when validation happens correctly. The conceptual entry point is RFC 4033: https://datatracker.ietf.org/doc/html/rfc4033
Think of DNSSEC as tamper-evident packaging. It does not hide the box. It proves nobody swapped the contents.
What DNSSEC does not do
DNSSEC does not encrypt. Your resolver still sees your queries. On‑path observers still see queries unless you also use DoT or DoH. Furthermore, DNSSEC can increase response sizes and operational complexity which means misconfigurations can cause real outages. That is why many teams validate at resolvers they control and monitor tightly.
DoH vs DoT: how to choose with an expert lens
The crypto story looks similar. Both use TLS. The real differences show up in deployment and control.
- Network governance: DoT fits OS-level and network-level policy more cleanly. DoH can bypass that policy when it is embedded in applications.
- Blocking resistance: DoH is harder to block without breaking the web. DoT is easier to block through port control.
- Complexity surface: DoH inherits the HTTP stack which expands implementation surface area. DoT stays closer to classic DNS plumbing.
- Observability: DoT keeps DNS identifiable as DNS. DoH buries it in 443 flows which complicates incident response.
- Centralization pressure: both can centralize DNS if clients default to a few big resolvers. DoH has accelerated that trend in some ecosystems.
So the “DoH vs DoT” decision is rarely purely technical. It is political. It is operational. It is about where you want the control plane to live.

The best setup: layered DNS privacy with integrity
There is no universal best setup. There is a best setup for your threat model. Still, a robust baseline looks consistent across serious deployments.
Best setup A: local validating resolver + DNSSEC + encrypted upstream
If you can run infrastructure at home or in a lab, this is the cleanest architecture.
- Run a local recursive resolver that performs DNSSEC validation.
- Forward upstream over DoT or DoH when you need privacy from your ISP.
- Keep caching local to reduce query exposure and improve latency.
This approach maximizes autonomy. It also gives you auditability. Unbound provides practical guidance for privacy features and DoH support: https://unbound.docs.nlnetlabs.nl/en/latest/topics/privacy/dns-over-https.html
Best setup B: OS-layer DoT with strong authentication plus DNSSEC where available
For fleets and servers, consistency matters more than cleverness.
- Enforce DoT at the OS or resolver layer.
- Use strict authentication guidance from RFC 8310 where possible.
- Validate DNSSEC in the resolver you control or in a trusted forwarder.
This reduces split DNS and it keeps browser behavior from defining your security posture.
Best setup C: browser DoH with strict anti-leak controls
Use this when networks interfere with DNS and you cannot control the local path.
- Pick a resolver with clear policy and a credible security track record.
- Disable plaintext fallback where feasible.
- Align browser and OS settings to avoid dual-resolver ambiguity.
Cloudflare’s encrypted DNS docs offer a pragmatic view of deployment considerations: https://developers.cloudflare.com/1.1.1.1/encryption/dns-over-https/
Failure modes that quietly defeat DNS privacy
Most breaches happen at seams.
- Plaintext fallback during network weirdness: captive portals and broken TLS inspection can trigger leaks.
- Split DNS between apps: browser DoH plus OS plaintext DNS creates inconsistent results and exposes queries.
- Trusting “encrypted” without validating identities: encryption to the wrong endpoint still loses.
- Assuming DNSSEC exists without validation: DNSSEC only works when a validator checks signatures.
- Ignoring resolver logging: your resolver can still profile you even with perfect transport encryption.
Three mental diagrams to keep your model honest
- Classic DNS path: client → recursive resolver → authoritative servers. Observers can read and inject at every hop.
- DoT vs DoH wrapping: DoT wraps DNS in TLS on a dedicated channel. DoH wraps DNS in HTTPS inside web flows.
- DNSSEC chain of trust: root → TLD → zone keys → signed records. Validation proves authenticity, not secrecy.
Bottom line
If you want practical DNS privacy, start by choosing where trust should live. Then layer controls.
Use DoT when you want clean governance and predictable operations. Use DoH when networks behave adversarially or block dedicated DNS privacy channels. Add DNSSEC validation to stop tampering and spoofing regardless of transport. That combination delivers privacy against on‑path observers and integrity against forged answers, which is what a modern DNS posture should actually mean.